Resources
Blog Authors
Blog Categories
Silver Sponsor
Resource Blogs

Cyber Crime Taking Down Cities
Earlier this year, in March, the City of Atlanta’s nearly 8,000 employees heard words they never thought they would hear: “It’s okay to turn your computers on.” Their computers were powered off for five days. In those five days Atlanta residents could not pay traffic tickets, water bills, or report city issues. Read how ransomware impacted this metropolitan area.
read more -->
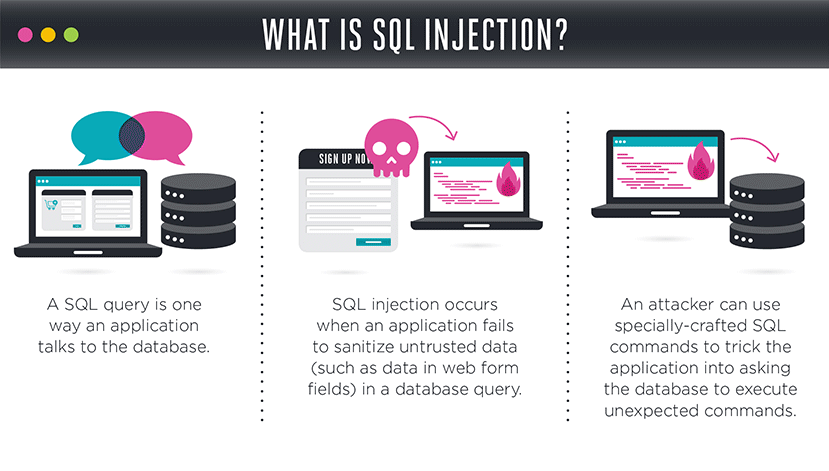
The Lethal Injection
Have you ever heard of SQL Injection?
If you’re thinking that it’s some type of cyber term, you’re right.
But, if you’re thinking that it won’t affect you, think again.
read more -->
Not Your Everyday Tool Kit
I recently had the chance to take a course in Penetration Testing, which is designed to teach you how to hack so that you know how to prevent getting hacked. Among the suite of tools I’ve been exposed to is the Social-Engineer Toolkit (SET). Read more on how you can leverage this tool and why you should be.
read more -->

Kidnapping Your Computer
Ransomware is no joke: It’s a type of malicious software used to block access to your data, or threatens to publish and/or delete the data until a ransom is paid to the hacker. Obviously, there’s no guarantee that paying a ransom will return access to you or information or that hacker won’t publish or delete the data. In turn, your computer’s stuck. Read about how you can protect.
read more -->

How is the Security Industry Responding to Infrastructure Threats?
More than 57,000 industrial control systems (known as SCADA – Supervisory Control and Data Acquisition) are connected to the Internet in our country, many with similarly conceived control systems. See how this impacts security and why we should all be concerned with cyber threats.
read more -->

Apps Designed to Make Your Smartphone Safer
Biometrics are a newer solution to an age old problem when it comes to cellphones. But using your fingerprint to unlock your phone is no longer a novelty. Have you thought about what happens when your fingerprints are stolen? When your photo is cloned? Read more to see what apps can make your smartphone smarter.
read more -->

Global State of Information Security
From April 4, 2016 to June 3, 2016, PricewaterhouseCoopers (PWC), and CXO Media (publications CIO, and CSO) conducted “The Global State of Information Security Survey 2017. While clearly meant for the IT sector, I found several areas of interest to the broader security market.
read more -->

The Internet of Things or The Internet of Trouble?
While attending SIA’s October Securing New Ground Conference, I was asked to moderate a session on the Internet of Things. Not quite sure what that means? Well, do you have a pacemaker? How about a DVR? The Internet of Things (IoT) refers to the billions of connected devices in our world—some say up to 200 billion devices will be connected by 2020.
read more -->

Pa55w0rd Pr0bl3ms
Sick and tired of forgetting your password for important information? Concerned that you use one password for everything? With the right software, you can update your technology and better secure your digital information.
read more -->

The IoT: Embrace Opportunity and Manage Risk
It seems like everything today is getting connected: your car, garage doors, refrigerator, phone, and camera—the list goes on. Security researchers have long warned that this relatively new technology comes with its own share of security issues (see our recent post on Brian Krebs for more background of the Internet of Things). But, how can we protect ourselves from the imposing risk in being constantly connected?
read more -->
The Internet of Trouble
Once defined and restricted by proprietary technology, the security industry has now become part of the movement embracing open connectivity and the Internet of Things, or IoT. The flexibility and simplicity of connecting devices and sensors to our systems is great, but it comes with new vulnerabilities and opened up the opportunity for more risk.
read more -->
Maintaining a Global Security Focus
Cyber security is an ever-growing problem, and for widespread operations, hunkering down in silos is probably not the answer. Here’s a few thoughts to apply to your global security team.
read more -->

Today's Top Trends in Cyber Security
Protecting information online should be a top priority for all. From encryption and decryption, to block chaining and protecting databases, we rounded up three of today’s most interesting trends in cyber security.
read more -->

IT Security in the Spotlight
PSA is aggressively taking a lead role in initiating an industry conversation and awareness of Cyber Security issues. Why PSA? The answer lies in its commitment to its owners, members, and partners to educate and position them to deliver the highest level of security to their customers. Today, that must include cyber security.
read more -->

Identity Management for More Secure Video
Presidential Executive Order 13636, 'Improving Critical Infrastructure Cybersecurity,' issued in February, 2013, called for the development of a voluntary risk-based Cybersecurity Framework - a set of industry standards and best practices to help organizations manage cybersecurity risks. Version 1.0 of the framework was published by NIST in February, 2014. The Framework focuses on business drivers to guide cybersecurity activities and on considering cybersecurity risks in the organization's risk management processes.
read more -->

Video Vulnerability Alert: Don't Get Shellshocked
In Sept. 2014, a vulnerability known as Shellshock (also known as Bashdoor) was discovered and disclosed. And that's potentially big news for organizations who operate, maintain or otherwise use Linux-based security equipment - which can now be considered vulnerable to hackers.
read more -->

Hack Attack
Recently, I have been included in an extensive e-mail thread initiated by PSA's CEO, Bill Bozeman. Bill's e-mail obviously struck a chord with the many people who were included in this communication. In part, Bill said, 'We are at the beginning of what I perceive to be a major finger pointing blame game in our niche as related to cyber security. Who is at fault if physical security devices are hacked and information that was incorrectly assumed to be secure by the end user is stolen? Will the manufacturer be held accountable? the integrator? the consultant?'
read more -->

We're Surrounded
It's no secret that megapixel cameras have taken the market by storm, providing the ability to see more with fewer cameras, with progressively better video quality and digital PTZ features. Conversely, fish eye lenses providing up to 360 degree images of varying quality have been around for years. So, it's not surprising that the combination of high pixel density sensors and appropriate lenses, enhanced by sophisticated image processing algorithms, has led to expanded product offerings in really good 180 degree and 360 degree panoramic IP cameras. Let's take a closer look at these three elements to see how they have combined to create this growing class of products.
read more -->

Lights, Camera..Activity
Newark Airport got quite a bit of press in February for its deployment of 171 LED light fixtures that form the backbone of a new wireless network that would not only control lighting, but also transmit data from security devices. The fact that surveillance cameras and activity sensors were to be part of this network caused a great deal of consternation - which tells me how little-informed the mainstream media, not to mention the public in general, really is when it comes to the potential of security technology.
read more -->

How Secure is the Physical Security Network?
That physical security has long passed the point of no return on its transition to being IP network-based is generally accepted in the industry. One can argue that a critical mass of designers, engineers and technicians (if not the salespeople) in the industry has been reached, to the point where most IP-based security systems generally work — streaming, displaying and recording video, locking and unlocking doors, providing audio over intercom, etc.
Granted, the industry has a long ways to go in creating a set of generally recognized certification credentials which bridge IT and physical security. So, now that the industry has more or less stumbled its way through this first “phase†of the technology shift, we must turn our attention to the next challenge — security of these physical security networks.
read more -->

Physical Security Network Management
One area within the subject of convergence that has received surprisingly little press, and that is conspicuously missing from industry product offerings, is Network Management targeted at the connected devices. The ISO defines five elements of network management: fault, configuration, accounting, performance and security. Some or all of these are implemented in a variety of Network Management Systems (NMS).
read more -->

