Resources
Blog Authors
Blog Categories
Silver Sponsor
Resource Blogs

Cyber Crime Taking Down Cities
Earlier this year, in March, the City of Atlanta’s nearly 8,000 employees heard words they never thought they would hear: “It’s okay to turn your computers on.” Their computers were powered off for five days. In those five days Atlanta residents could not pay traffic tickets, water bills, or report city issues. Read how ransomware impacted this metropolitan area.
read more -->
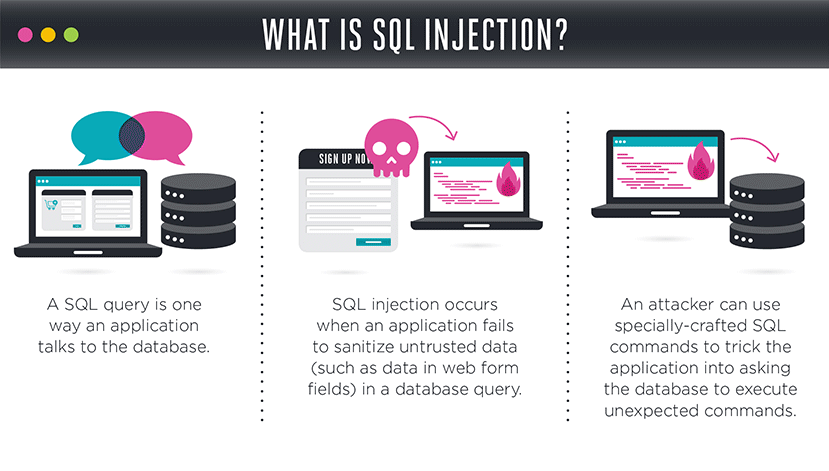
The Lethal Injection
Have you ever heard of SQL Injection?
If you’re thinking that it’s some type of cyber term, you’re right.
But, if you’re thinking that it won’t affect you, think again.
read more -->
Not Your Everyday Tool Kit
I recently had the chance to take a course in Penetration Testing, which is designed to teach you how to hack so that you know how to prevent getting hacked. Among the suite of tools I’ve been exposed to is the Social-Engineer Toolkit (SET). Read more on how you can leverage this tool and why you should be.
read more -->

Why Artificial Intelligence is Crucial to Cyber Security
Artificial Intelligence or AI is so much more than virtual reality, robots, and video games. In fact, a lot of AI development is spent in the cyber security space: especially with the creation of ransomware and more sophisticated malware.
Microsoft, Google, Cisco, Symantec, and more of the top tech companies in the world are all investing on enhancements around AI and cyber security. But how?
read more -->

How is the Security Industry Responding to Infrastructure Threats?
More than 57,000 industrial control systems (known as SCADA – Supervisory Control and Data Acquisition) are connected to the Internet in our country, many with similarly conceived control systems. See how this impacts security and why we should all be concerned with cyber threats.
read more -->

Apps Designed to Make Your Smartphone Safer
Biometrics are a newer solution to an age old problem when it comes to cellphones. But using your fingerprint to unlock your phone is no longer a novelty. Have you thought about what happens when your fingerprints are stolen? When your photo is cloned? Read more to see what apps can make your smartphone smarter.
read more -->

Global State of Information Security
From April 4, 2016 to June 3, 2016, PricewaterhouseCoopers (PWC), and CXO Media (publications CIO, and CSO) conducted “The Global State of Information Security Survey 2017. While clearly meant for the IT sector, I found several areas of interest to the broader security market.
read more -->

Big Data and Privacy for Physical Security
Examines the business expectations regarding big data supported security technology including privacy.
read more -->

Today's Top Trends in Cyber Security
Protecting information online should be a top priority for all. From encryption and decryption, to block chaining and protecting databases, we rounded up three of today’s most interesting trends in cyber security.
read more -->

Identity Management for More Secure Video
Presidential Executive Order 13636, 'Improving Critical Infrastructure Cybersecurity,' issued in February, 2013, called for the development of a voluntary risk-based Cybersecurity Framework - a set of industry standards and best practices to help organizations manage cybersecurity risks. Version 1.0 of the framework was published by NIST in February, 2014. The Framework focuses on business drivers to guide cybersecurity activities and on considering cybersecurity risks in the organization's risk management processes.
read more -->

Video Vulnerability Alert: Don't Get Shellshocked
In Sept. 2014, a vulnerability known as Shellshock (also known as Bashdoor) was discovered and disclosed. And that's potentially big news for organizations who operate, maintain or otherwise use Linux-based security equipment - which can now be considered vulnerable to hackers.
read more -->

The Latest in Lighting and Power
Raytec (www.rayteccctv.com) has offered network controllable lighting for about two years, and a new wrinkle I recently noticed was powering the light via 'high PoE'. Two not-so-new innovations make this possible - high efficiency LED light sources and high PoE levels which go beyond the IEEE 802.3at PoE+ standard.
read more -->

Hack Attack
Recently, I have been included in an extensive e-mail thread initiated by PSA's CEO, Bill Bozeman. Bill's e-mail obviously struck a chord with the many people who were included in this communication. In part, Bill said, 'We are at the beginning of what I perceive to be a major finger pointing blame game in our niche as related to cyber security. Who is at fault if physical security devices are hacked and information that was incorrectly assumed to be secure by the end user is stolen? Will the manufacturer be held accountable? the integrator? the consultant?'
read more -->

Converging on Convergence
If the end point for where the explosion of network devices and available data is what we are coming to know as big data, it's useful to think about 'convergence' as a journey to that end. So the beginning of this journey today is from a position I'll call 'little data', or the information from a closed security system - cameras, some storage, video management, and often a tie into access control, loosely or tightly integrated.
read more -->

Lights, Camera..Activity
Newark Airport got quite a bit of press in February for its deployment of 171 LED light fixtures that form the backbone of a new wireless network that would not only control lighting, but also transmit data from security devices. The fact that surveillance cameras and activity sensors were to be part of this network caused a great deal of consternation - which tells me how little-informed the mainstream media, not to mention the public in general, really is when it comes to the potential of security technology.
read more -->

SNMP Primer
SNMP ... today, this could mean “Security - Not My Protocol†for all the use we’re getting out of it. What SMP officially stands for is Simple Network Management Protocol. You may have seen it on a configuration screen for an IP camera or other security device and wondered what it was used for. It really is a pretty useful protocol, and it’s time we did something with it.
read more -->

Video Storage: Take a Big Byte
Terabytes, petabytes, exabytes, zettabytes, brontobytes...what’s our security world coming to?
When you combine the trends of more surveillance cameras, higher bandwidth requirements, fatter bandwidth pipes and the continuing decline in storage costs, you get near-exponential growth in bytes stored. The question is, how do we manage this vast amount of video data? I’ve discussed this question with several large-scale storage vendors recently and learned some very interesting things.
read more -->

Video at your Service
The major product sectors of the security industry seem to have all followed a similar progression: analog (or low-speed serial), to digital, to IP, and now, to the cloud. The security industry may be lagging behind the IT world in terms of standards, features and product applications; however, they are both traveling the same path — and it leads to the cloud.
Just look at the video market: VCRs are extinct, hybrid DVRs bridge the analog and digital worlds, and NVRs and dedicated or shared storage equipment reside on networks, accessed by an array of video management products. Thus, off-site video storage and monitoring, implemented through the Internet (the “cloudâ€), is becoming a real business. IMS Research points out that the Video Surveillance as a Service (VSaaS) market was approximately $500 million in 2011 and could reach $1 billion by 2014.
read more -->

How Secure is the Physical Security Network?
That physical security has long passed the point of no return on its transition to being IP network-based is generally accepted in the industry. One can argue that a critical mass of designers, engineers and technicians (if not the salespeople) in the industry has been reached, to the point where most IP-based security systems generally work — streaming, displaying and recording video, locking and unlocking doors, providing audio over intercom, etc.
Granted, the industry has a long ways to go in creating a set of generally recognized certification credentials which bridge IT and physical security. So, now that the industry has more or less stumbled its way through this first “phase†of the technology shift, we must turn our attention to the next challenge — security of these physical security networks.
read more -->

Physical Security Network Management
One area within the subject of convergence that has received surprisingly little press, and that is conspicuously missing from industry product offerings, is Network Management targeted at the connected devices. The ISO defines five elements of network management: fault, configuration, accounting, performance and security. Some or all of these are implemented in a variety of Network Management Systems (NMS).
read more -->

